In this article, I’m going to mention about Secure Hash Algorithm 1 (SHA1), which is one of the most widely used crypto algorithms that I have used and learned while developing an Android mobile application.
SHA1: I would like to indicate there are SHA0, SHA2, SHA3, MD5 algorithms as well as SHA1 algorithm.
In short:
SHA2: SHA2 is used in some security applications and protocols which is used commonly such as TLS, SSL, PGP, SSH, S/MIME and IPsec.
SHA3: SHA3 is the last member of Secure Hash Algorithm family. Although it is part of the same standard series, SHA3 is quite different internally from the MD5-like structure of SHA1 and SHA2.
MD5: MD5 (Message-Digest algorithm 5) is a widely used cryptographic digest function. Regardless of the size of the input data, it generates a 128-bit hash value.
HASH: The hash generates by determining the key from within given word.If the entered password is correct, it extracts the key words in this hash text and finds them by comparing them with the original. This hash value is 128.
(Collisions): One of the issue of hash encryption algorithms is collisions. Collision, after two data encryption process, is due to the same digest. MD5 algorithm, which can be defined as the most widely used encryption algorithm beside SHA1, generates a 128-bit hash value. In this case, testing 264 times is enough to find the collision. In the SHA1 algorithm, this situation has been safer by generating 160-bit hash and by increasing to 280 the security level to prevent collision.
SHA-1 (Secure Hash Algorithm 1)
SHA1 uses an entry of up to 264 bits and generates 160-bit hash value, it can provide 80 bit security to not any conflict. This algorithm is only used for encryption. It is not an algorithm based on decryption. It is assumed that the original data can not be recovered from the generated hash. SHA1 algorithm is used for e-mail encryption applications, secure remote access applications, private computer networks etc. The biggest difference of SHA1, which works same principle MD5, is it can provide database management. It exposes a hash text using bitwise logic operations.
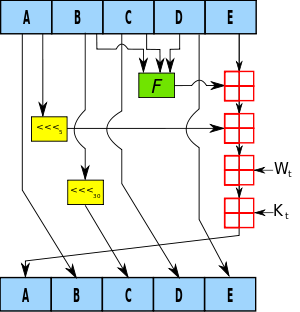
During this process, 512-bit blocks are allocated and if the bit is not enough, 512 bits are completed by adding to the last bit sequences. This 512-bit text is divided into 16 16-bit message fragments, and After applying a normal four operation for each message thread, the Left Shift operation is performed. This process is repeated 4 times, resulting in a 160-bit cipher sequence.
Learning SHA1 Value for Android
In order to get Google API KEY in one of my projects I had to learn SHA1 value. I wanted to develop the project on Linux. I did not have much idea about it and I continued on Windows first because I quickly got to SHA1 on Windows. As I started to research for Linux, I noticed that it could be found much faster on the terminal screen. I will share examples for both.
There are two options for SHA: We will test it as an APK or in the emulator environment as a debug. It means Release or debug certificate. In short, I need to create the APK file of the application for the Release and look at the SHA section.
For Windows:
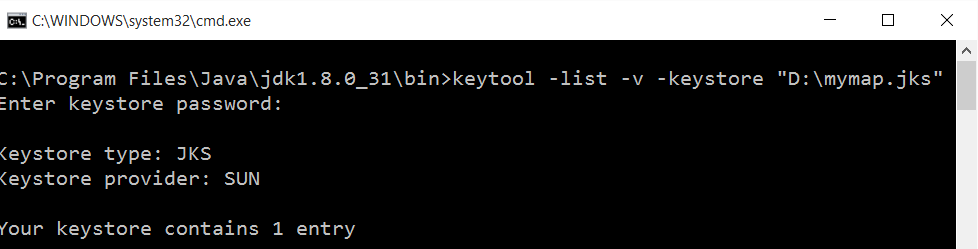
Assuming that you created your APK file and that your Java JDK installed, we will open this folder. Example: C:\Program Files\Java\jdk1.8.0_31\bin
Here click on the right button on a mouse and shift all at once, you will see ‘run CMD’ option. For those who may would like, there is a video: Google Maps API Key Oluşturma
keytool -list -v -keystore “Key Yolu”
Here is “Key Yolu” file path of .jks for APK we created. Once you’ve written this, you can learn SHA1 information.
For Linux:
Assuming that you created your APK file and that your Java JDK installed, for Linux as well, paste below code to console
keytool -list -v -keystore ~/.android/debug.keystore -alias androiddebugkey -storepass android -keypass android
run the code and get SHA1 value. Then save SHA1 value. You can use Google API and go on develop your project anymore.
Sources:
[1] Şifreleme Algoritmaları – SHA1, https://webmaster.kitchen/sifreleme-algoritmalari-sha1/
[2] Secure Hasing Algorithm (SHA), http://bilgisayarkavramlari.sadievrenseker.com/2009/11/02/secure-hasing-algorithm-sha/
[3] SHA-1, https://www.wikiwand.com/tr/SHA-1
[4] SHA1 Şifreleme Metodu, https://bidb.itu.edu.tr/seyirdefteri/blog/2013/09/08/sha1-şifreleme-metodu
